Network Access Servers
|
A Network Access Server (NAS) is a device designed to provide remote access to a network.
There are many different types of NAS systems for use with TCP/IP networks including
serial terminal access controllers, modem pools or stacks, ISDN routers, and multi-function
access controllers. These types of equipment share several common characteristics;
switched service connections, point-to-point serial IP protocols, and user authentication.
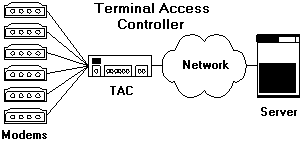
A Terminal Access Controller (TAC) is a piece of equipment that has one or more serial ports and one or more network connections. In TCP/IP networks this is normally a device with RS-232C serial ports and an Ethernet or Token Ring connector. Most of these will have POTS modems or ISDN terminal adapters connected so they can service incoming telephone calls.
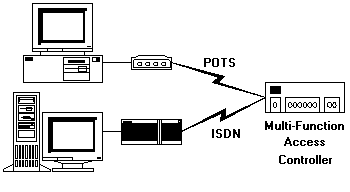
 The term Modem Pool or Modem Stack usually refers to a single piece of equipment with multiple internal modems. Most of these consist of a host enclosure with add-in option cards that manage one, two, four, or more modems per card. Some of these connect each modem to an individual telephone cable. Others can accept one or more T1 circuits with up to 24 individual POTS lines on a single circuit, distributing the incoming calls across the modem cards. Some modem stacks have a discrete serial connector for each modem used for connecting to a serial TAC, and some have an integrated connector that gives them direct access to the network. ISDN routers are devices intended to connect ISDN digital telephone service directly to a network. Some ISDN routers accept one or more Basic Rate Interface (BRI) ISDN circuits and some accept one or more Primary Rate Interface (PRI) ISDN circuits. A typical BRI circuit has two bearer lines, each equivalent to one POTS voice line and each capable of handling an independent connection at speeds up to 64k baud. Most BRI routers can also combine the two BRI channels into a single 128k baud connection. A typical PRI circuit is delivered on a T1 line and carries 23 bearer lines and one control line. Each bearer line can carry an independent connection at speeds up to 64k baud, and multiple bearer connections can be aggregated for higher speed connections. Most ISDN routers have one or more network connections for Ethernet or Token Ring networks. Multi-Function Access Controllers are devices that allow the user to add option cards for combinations of serial connections, POTS modems, ISDN BRI and PRI circuits, and network connections. Many of these devices are very high speed systems with flexible configuration and management software. Some of these devices are capable of determining, at the time a call is received, whether it is from a POTS modem, ISDN terminal adapter or router, or other device. They can then pass the connection to the proper circuit for management.
 The term, Switched Service, refers to a communications connection that can be dynamically connected to one of many destinations, or one to which connections can be made from multiple sources. The switched service that most people are familiar with is the standard telephone system. By dialing a telephone number a call can be placed to one particular destination out of all of the telephones in the world. ISDN is another switched service that uses the same international telephone system to place digital calls. Switched services do not have to use the public telephone network. There are many different types of switched services available from telecommunication service providers, such as Switched 56k and X.25 Packet Switch service. The reason that switched service is important to remote access is that it allows multiple remote users to connect to and share the resources of a network. Most NAS systems designed to manage TCP/IP connections support SLIP and/or PPP point-to-point IP protocols. This allows the system to establish and manage the individual communications links to the remote sites across the switched service. Depending on the manufacturer of the equipment and the software used to manage it, some systems require a separate IP address for each end of each communications link. Others use one IP address for each connection and a single address for the NAS system. Almost all NAS systems authenticate users before allowing access to a network. Most allow a network administrator to store one or more ID and Password pairs on the NAS system itself and can use these for authentication. Many systems also provide some method for the NAS system to contact an authentication server across the network to validate the ID and Password, and to record usage activity. Using remote authentication an NAS system can contact a server on the same local network segment or anywhere else on any connected TCP/IP network. Many ISPs provide dial-in service in remote areas by placing just the NAS equipment at the remote site. The NAS then contacts an authentication server at a central network operations center for user authentication and usage logging. There are two common protocols used for NAS authentication, TACACS and RADIUS. Though both of these are implemented as higher level protocols, it is appropriate to discuss them in the Network Access Layer protocols because they are normally used to supplement PPP and SLIP. TACACSThe Terminal Access Controller Access Control System (TACACS) is a remote authentication protocol adopted and developed by Cisco Systems, a major networking equipment manufacturer. When a dial-in connection attempts to authenticate using PAP or CHAP, a NAS system using TACACS will contact an authentication server across the network and request verification. This verification may include not only the ID and Password, but other parameters including the line the call is on and requests to use a specific IP address or host name. The TACACS server validates the request against a database on the server, logs the activity, and sends an approval or denial to the NAS system. TACACS also allows the NAS system to log information to the authentication server when the communications link is terminated.Cisco has continued to develop and expand TACACS, and has released an extended version of TACACS called TACACS+. This extended protocol allows for various additional features including encryption and extended user activity logging. The original TACACS protocol was loosely documented in RFC 1492, and information on the TACACS+ enhancements is available from Cisco. TACACS was primarily developed by Cisco for use with its own routers and NAS systems, and some of the definition of the protocol has been considered proprietary by Cisco. TACACS server software from Cisco is available on most UNIX systems as well as for some Microsoft Windows based systems. Example server code is freely available from Cisco, and there are some third party TACACS authentication server software packages that are available as well. RADIUSThe Remote Authentication Dial In User Service (RADIUS) is a remote authentication protocol developed by Livingston Enterprises, Inc., a major networking equipment manufacturer. RADIUS is a protocol that provides the same basic suite of NAS authentication services provided by TACACS.Though RADIUS was primarily developed by Livingston for support of its own NAS products, the protocol definition is well documented and publicly available in RFC 2058 as an Internet standard. RADIUS authentication server software from Livingston and third party sources is widely available for most major network server hardware and software platforms. This has resulted in RADIUS being adopted as a remote authentication protocol by many other NAS system suppliers.
|